Published On Mar 22, 2023
DISCLAIMER:
STRICTLY FOR EDUCATION PURPOSES ONLY.
ANYTHING SHOWN IN THIS VIDEO IS SRICTLY FOR EDUCATION PURPOSES ONLY AND PERFORMED UNDER A CONTROLED ENVIRONMENT.
DON'T TRY THESE STEPS ON ANY REAL WEBSITE. THE AUTHOR IS NOT RESPONSIBLE FOR ANY CONSEQUENCES.
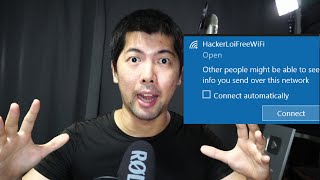
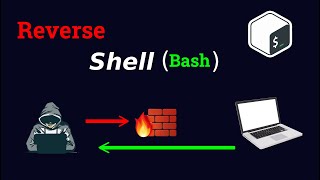
Maintaining access is a critical component of a successful cyberattack. Once a hacker gains access to a target system, they need to ensure that they can maintain access for as long as possible to continue their malicious activities. One technique for maintaining access is using a reverse shell created using netcat.
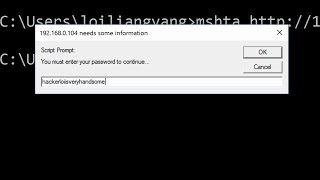
Netcat is a versatile network tool that can be used for a variety of purposes, including creating a reverse shell. A reverse shell allows a hacker to establish a connection to the target system from a remote machine, giving them access to the target system's command prompt.
Once the reverse shell is established, the attacker can execute commands on the target system remotely, providing them with continued access to the target system.
To protect against attacks using reverse shells and netcat, it is important to implement proper access controls, limit network traffic, and monitor for unusual network activity. Regularly scanning systems for vulnerabilities and applying security patches can also help prevent unauthorized access.
In summary, maintaining access is critical for a successful cyberattack, and techniques such as using a reverse shell created with netcat can help achieve this. However, it is important to use such techniques ethically and responsibly, and to take appropriate measures to protect against unauthorized access.